Listen now
Understanding the Complex Landscape of Digital Assets
In a world where our digital footprint spans across multiple platforms, networks, third-party software vendors, and devices, the role of attack surface management in cybersecurity has taken center stage. Like a sprawling city, every business – large or small – has an array of digital assets scattered across vast landscapes, both visible and hidden. These digital ‘properties’ form your attack surface, a playground ripe for cyber threats. From forgotten accounts to cloud misconfigurations to third-party software vulnerabilities, it’s a never-ending race to identify these potential risks and secure them.
The Aha Moment
Fresh out of undergrad, I witnessed this challenge firsthand while working as a security consultant at Accenture. Incumbent solutions struggled to surface all digital assets (IoT devices, VMs, containers, air-gapped endpoints, third-party software, network appliances, to name a few) and prioritize their weakest points. According to HackerOne’s 2022 Attack Resistance Report, one-third of large enterprise security teams observe less than 75% of their attack surface and almost one-fifth believe that more than 50% is unknown or not observable. I’ve personally seen sophisticated security organizations managing the inventory of legacy assets on an Excel spreadsheet!
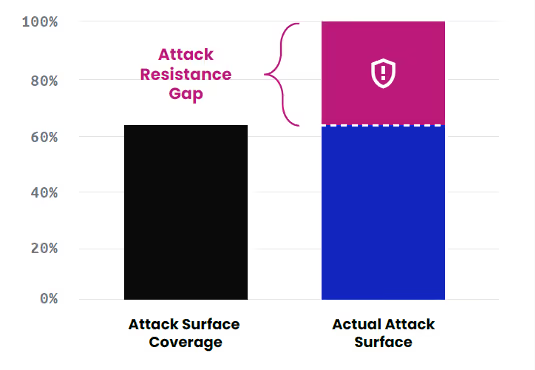
This was the aha moment. As an investor focused on cybersecurity, I am excited about innovative founders breaking out of the old guard of agent-based scanners and developing technologies that are fit for the modern IT environment.
How the Evolution of the IT Stack is Expanding the Attack Surface
The cloud paradigm and the move to a user-centric SaaS environment (see our article on PLG) greatly accelerated the digital transformation journey of large enterprises. This led to a proliferation of new digital assets and shadow IT (applications and systems outside of the purview of IT), both within and outside traditional network perimeters. This expansion came with many benefits including the faster adoption of innovative technologies, software development agility, and distributed workforce capabilities. However, in parallel, led to an explosion of new vulnerabilities that were growing faster than security teams could keep up. HackerOne’s 2022 Hacker Powered Security Report found 65,000 vulnerabilities in the enterprise with vulnerability types introduced by digital transformation growing the fastest, including misconfigurations and improper authorization growing by 150% and 45% respectively. The 2020 SolarWinds attack infected over 18,000 customers and went undetected for months, demonstrating the cyber risk of third-party software assets—an attack vector not identified by traditional scanners.
The New Guard is Here: Attack Surface Management

The security community has spoken with Gartner officially coining the term Attack Surface Management in late 2019. The two critical emerging categories within this larger umbrella are CAASM (Cyber Asset Attack Surface Management) and EASM (External Attack Surface Management). These two strategies are complementary and designed to identify, manage, prioritize, and secure all assets in the modern technology stack, thereby reducing the attack surface and enhancing overall security posture.
Cyber Asset Attack Surface Management (CAASM) is designed to address the ongoing challenges of asset visibility and vulnerability detection that security teams face. CAASM platforms typically take an agentless approach, providing a comprehensive view of all assets, both internal and external, by integrating with existing tools and assets via APIs. New software deployments, system updates, or changes in network configuration can rapidly alter an organization’s attack surface. Therefore, CAASM ensures that these changes are monitored and managed effectively, reducing the risk of security incidents.
On the other hand, External Attack Surface Management (EASM) focuses on the organization’s externally facing digital assets, such as web applications, third-party software vendors, and cloud-based service misconfigurations. These assets, accessible from the internet, represent low-hanging fruit for threat actors. EASM aims to minimize these potential attack vectors, thereby enhancing the organization’s security posture.
Why CISOs Should Explore Attack Surface Management Startups
Identifying vulnerabilities across organization's attack surface is crucial, but it can be a challenging task. Let's dive into why CAASM and EASM should be integral components of a successful enterprise security strategy:
1. Enterprise Security Sprawl
As the attack surface continues to grow in complexity, the number of security tools deployed in large enterprises has grown with it. Anomali’s 2022 Cybersecurity Insights Report estimates that the average enterprise has 130 security tools in production. Attack surface management platforms aggregate the growing set of siloed data sources across the security stack to provide a single pane of glass for more effective visibility and remediation.
2. The Rising Complexity of Enterprise Infrastructure
Traditional approaches to IT security, which focused on agent-based scanning, are no longer sufficient. The rise of cloud computing, remote work, and digital transformation initiatives has blurred the boundaries of what is considered an asset. Today's IT ecosystems are distributed, with numerous assets scattered across various locations, and many microservices and cloud-based applications are not compatible with agent-based scanners. Manual asset tracking via excel spreadsheets, homegrown scripts, or configuration management databases lacks efficient, comprehensive asset discovery and management. This necessitates a shift in focus from securing endpoints to securing all connected assets for holistic monitoring and is the main value driver of the next generation of asset management platforms like Axonius or JupiterOne.
3. Shadow IT Concerns
Shadow IT poses significant security risks. Shadow IT refers to IT systems, software, devices, services, and applications used without explicit organizational approval. While these tools can drive innovation and productivity, they also introduce additional attack vectors, as they often fall outside the purview of IT and Security teams. CAASM and EASM platforms can help uncover these shadow IT assets through API-based discovery, bringing them under the umbrella of the organization's security strategy.
4. The Importance of Prioritization
Every security professional will attest that the number of vulnerabilities (critical or otherwise) is continuing to grow faster than SOC analysts can remediate them, and the sheer volume of data generated by multiple security tools is overwhelming. To make matters worse, there is a clear shortage of security professionals needed for full coverage. CAASM and EASM platforms can help prioritize threats, providing actionable insights that enable organizations to respond effectively.
Embracing the Future of Cybersecurity with CAASM and EASM
The rise of CAASM and EASM reflects the evolving nature of cybersecurity. As businesses continue to navigate the digital landscape, these new startups will play an increasingly important role in their security toolkit. By embracing CAASM and EASM, organizations can not only protect their digital assets but also foster a culture of security that permeates through every aspect of their operations.
The future of cybersecurity is here, and it is continuous, external, and relentlessly proactive. At NGP, we understand the challenge enterprises face in extracting high-value insights from their complex environments, that’s why we continue to partner with innovative founders looking to disrupt traditional security domains—check out this piece on why we invested in SecurityScorecard, a leader in security risk ratings. If you have any questions or feedback related to the post, feel free to reach out via LinkedIn or send me an email at eric@ngpcap.com.
Photo by GuerrillaBuzz on Unsplash

.svg)






.svg)









